Nairobi says it has shut down illegal recruiters and will urge Moscow to sign a deal banning conscription.
Source link
Category: Uncategorized
-

Kenya to confront Russia over 'unacceptable' use of its nationals in combat
-

Trump threatens to block opening of US-Canada bridge
The Gordie Howe International Bridge, which connects Michigan to Ontario, is set to open this year.
Source link -
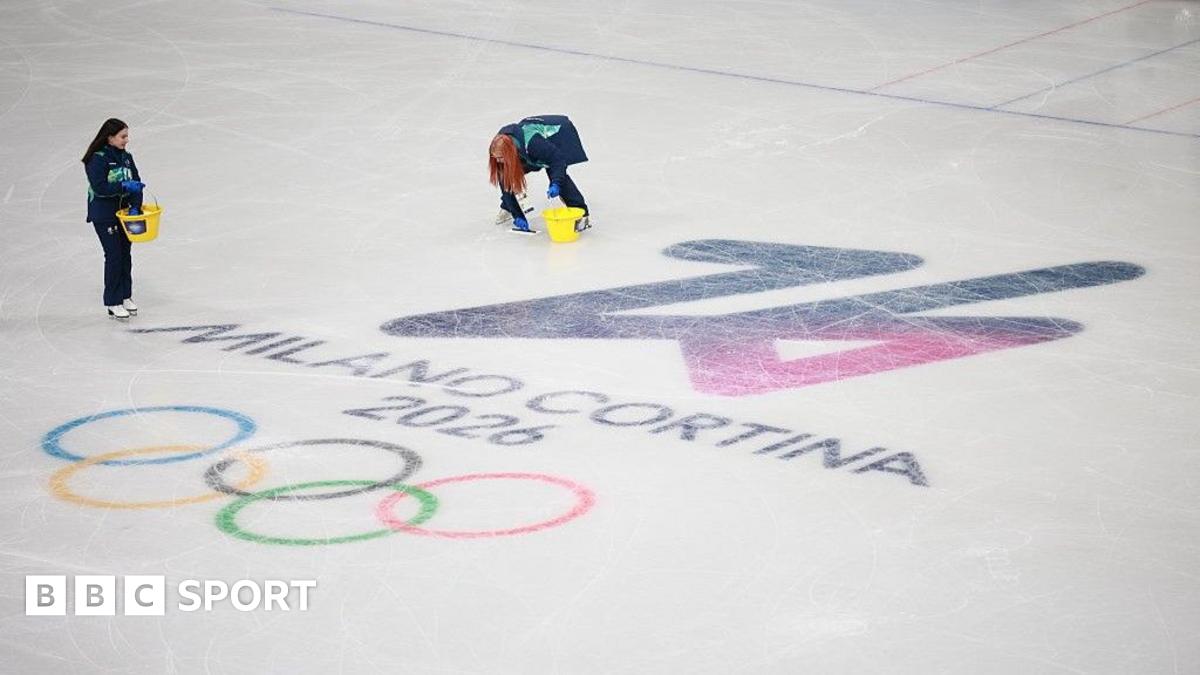
Winter Olympics 2026: What is Olympic ice and how is it made?
Olympic ice describes the uniform ice surface specified for international competitions, including the Winter Olympics.
Skilled technicians are responsible for making and maintaining the ice and they are are known as ‘ice masters’.
The team is tasked with ensuring the surface is optimal for the athletes to compete on in sports such as curling, ice skating and ice hockey.
The ice hockey arena in Milan-Cortina was built from scratch for the men’s and women’s matches following delays, concerns and last-minute building works.
But how do they make the ice for the rink?
It all starts with five centimetres of insulation laid down on the concrete floor. A vapour barrier is placed on top of the insulation, before engineers lay mats containing glycol on top to keep the ice cold.
Boards and glass walls are then placed around the rink and then roughly two inches of water is added above the mat – this is when the ice sheets are created.
The surface is painted white and sealed, with ice hockey markings and logos added.
Finally, the rink is topped with three to four centimetres of water to create the playing field. Temperatures are kept between -5 and -4C.
Resurfacing machines, colloquially known as Zambonis, are sent out regularly to shave away ice and form a new smooth layer.
Ice master Mark Messer, who is overseeing the long track speed skating said the hardest part is “working with a new system for such a high profile event, with little time for preparation”.
He added that although ice has been made on temporary settings, it has not been done on this scale for an Olympic Games.
Milan-Cortina will be the first time a temporary venue has been used for long track speed skating at a Winters.